Build And Secure Networks In Google Cloud - Cloud
- User Authentication: Identity-Aware Proxy
- Multiple VPC Networks
- VPC Networks - Controlling Access
- HTTP Load Balancer with Cloud Armor
- Create an Internal Load Balancer
- Google Cloud Packet Mirroring with OpenSource IDS
User Authentication: Identity-Aware Proxy
- Theory
- Authenticating users of your web app
- Identity-Aware Proxy (IAP) is a Google Cloud service that intercepts web requests sent to your application, authenticates the user making the request using the Google Identity Service, and only lets the requests through if they come from a user you authorize
- Deploy Application and Protect it with IAP
- Download the code
gcloud app deploy-=> Deploy the app to the App Engine Standard environment for Pythongcloud app browse-=> To view your application
- Access User Identity Information
- Two lines in main.py that get the IAP-provided identity data
user_email = request.headers.get('X-Goog-Authenticated-User-Email') user_id = request.headers.get('X-Goog-Authenticated-User-ID')
- Two lines in main.py that get the IAP-provided identity data
- Restrict Access with IAP
- In the cloud console window, click the Navigation menu > Security > Identity-Aware Proxy
- Click ENABLE API > Click GO TO IDENTITY-AWARE PROXY > Click CONFIGURE CONSENT SCREEN
- Select Internal under User Type and click Create
- Fill in the required blanks with appropriate values
- Click SAVE AND CONTINUE > BACK TO DASHBOARD
gcloud services disable appengineflex.googleapis.com-=> To disable the Flex API- If the Flex API is enabled, Google Cloud will look for a Flex Service Account
- Click the toggle button in the IAP column in the App Engine app row to turn IAP on
- Cryptographic Verification
- If there is a risk of IAP being turned off or bypassed, your app can check to make sure the identity information it receives is valid
- This uses a third web request header added by IAP, called X-Goog-IAP-JWT-Assertion
- The value of the header is a cryptographically signed object that also contains the user identity data
- Digital signature verification requires several extra steps, such as retrieving the latest set of Google public keys
- To retrieve and verify the cryptographically signed identity information
def user(): assertion = request.headers.get('X-Goog-IAP-JWT-Assertion') if assertion is None: return None, None info = jwt.decode( assertion, keys(), algorithms=['ES256'], audience=audience() ) return info['email'], info['sub']
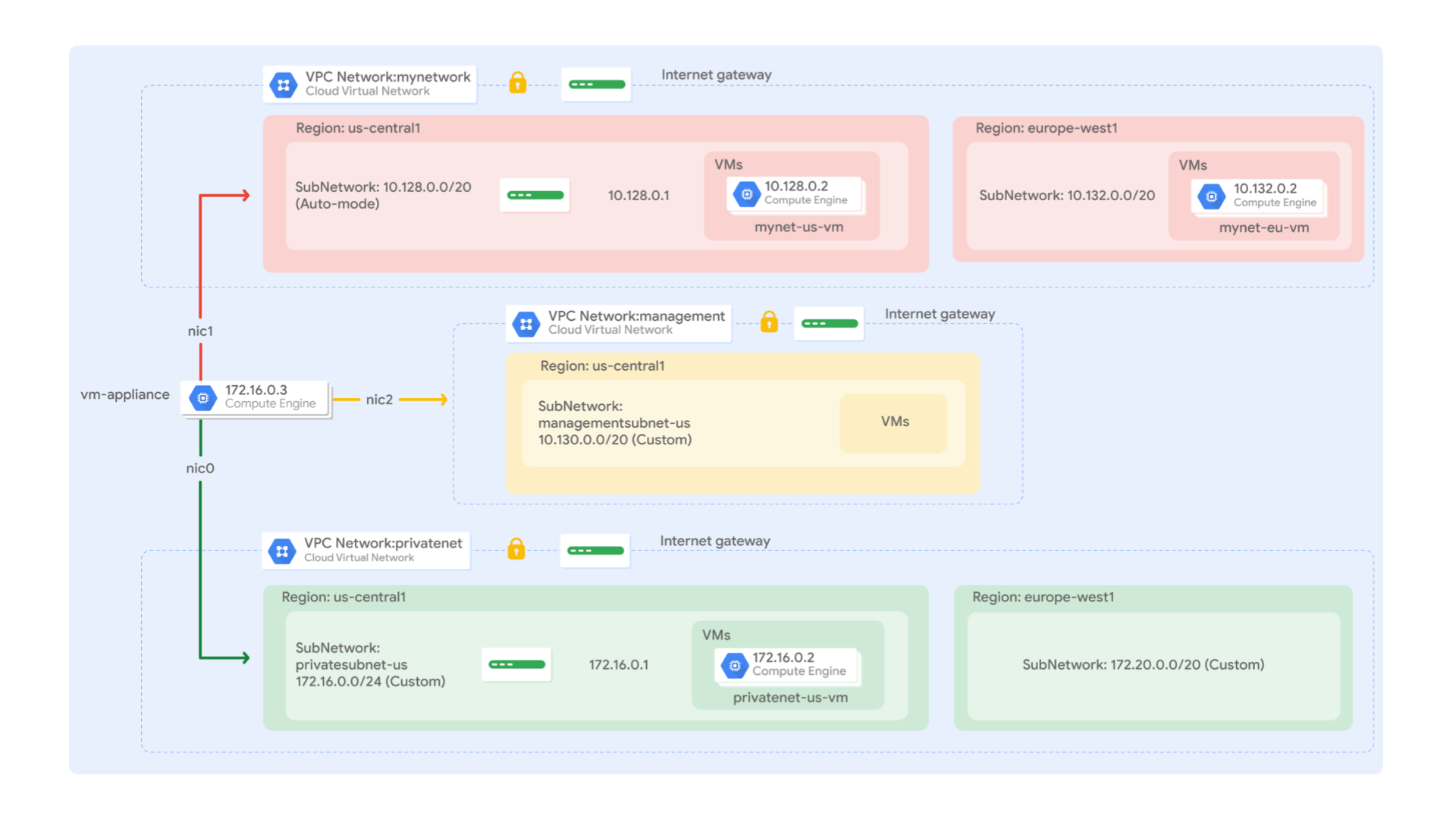
Multiple VPC Networks
- Theory
- Create custom mode VPC networks with firewall rules
- Create two custom networks managementnet and privatenet, along with firewall rules to allow SSH, ICMP, and RDP ingress traffic
- In the Cloud Console, navigate to Navigation menu > VPC network > VPC networks > Create VPC Network
- Set Name
- For Subnet creation mode, click Custom
- Fill other required values
- Click Done > Create
- Using Command Line
gcloud compute networks create privatenet --subnet-mode=custom-=> Create networkgcloud compute networks subnets create privatesubnet-us --network=privatenet --region=us-central1 --range=172.16.0.0/24-=> Create subnetgcloud compute networks list-=> List the available VPC networksgcloud compute networks subnets list --sort-by=NETWORK-=> List the available VPC subnets (sorted by VPC network)- `` -=>
- Create the firewall rules for managementnet
- Navigation menu > VPC network > Firewall > Create Firewall Rule
- Set required values > Create
- Using Command Line
gcloud compute firewall-rules create privatenet-allow-icmp-ssh-rdp --direction=INGRESS --priority=1000 --network=privatenet --action=ALLOW --rules=icmp,tcp:22,tcp:3389 --source-ranges=0.0.0.0/0gcloud compute firewall-rules list --sort-by=NETWORK-=> List all the firewall rules (sorted by VPC network)
- Create VM instances
gcloud compute instances create privatenet-us-vm --zone=us-central1-f --machine-type=n1-standard-1 --subnet=privatesubnet-usgcloud compute instances list --sort-by=ZONE-=> List all the VM instances (sorted by zone)
- Explore the connectivity between VM instances
ping -c 3 <Enter IP here>- No internal IP address communication is allowed between networks, unless you set up mechanisms such as VPC peering or VPN
- Create a VM instance with multiple network interfaces
- Multiple network interfaces enable you to create configurations in which an instance connects directly to several VPC networks
sudo ifconfig-=> List the network interfaces within the VM instanceip route-=> List the routes for an instance
VPC Networks - Controlling Access
- Create the web servers
- While creating Click NETWORKING, DISKS, SECURITY, MANAGEMENT, SOLE-TENANCY > Networking > Add a tag
- Install nginx and customize the welcome page
sudo apt-get install nginx-light -y-=> In the SSH terminal to install nginxsudo nano /var/www/html/index.nginx-debian.html-=> Open the welcome page in the nano editor- Press CTRL+o, ENTER, CTRL+x to save and exit
cat /var/www/html/index.nginx-debian.html-=> Verify the change
- Create the firewall rule
- Navigation menu > VPC network > Firewall > Create Firewall Rule
gcloud compute instances create test-vm --machine-type=f1-micro --subnet=default --zone=us-central1-a-=> Create a test VMcurl ipAddress-=> Test connectivity in SSH terminal
- Explore the Network and Security Admin roles
- Network Admin -=> Permissions to create, modify, and delete networking resources, except for firewall rules and SSL certificates
- Security Admin -=> Permissions to create, modify, and delete firewall rules and SSL certificates
gcloud compute firewall-rules delete allow-http-web-server-=> To delete the allow-http-web-server firewall rule
- Create a service account
- Navigation menu > IAM & admin > Service Accounts > Create service account
- Click on three dots > Manage Keys > Add Key > Create new key > Create to download your JSON output
- To upload credentials.json through the SSH VM terminal, click on the Upload file icon in the upper-right corner
gcloud auth activate-service-account --key-file credentials.json-=> Authorize the VM with the credentials you just uploaded
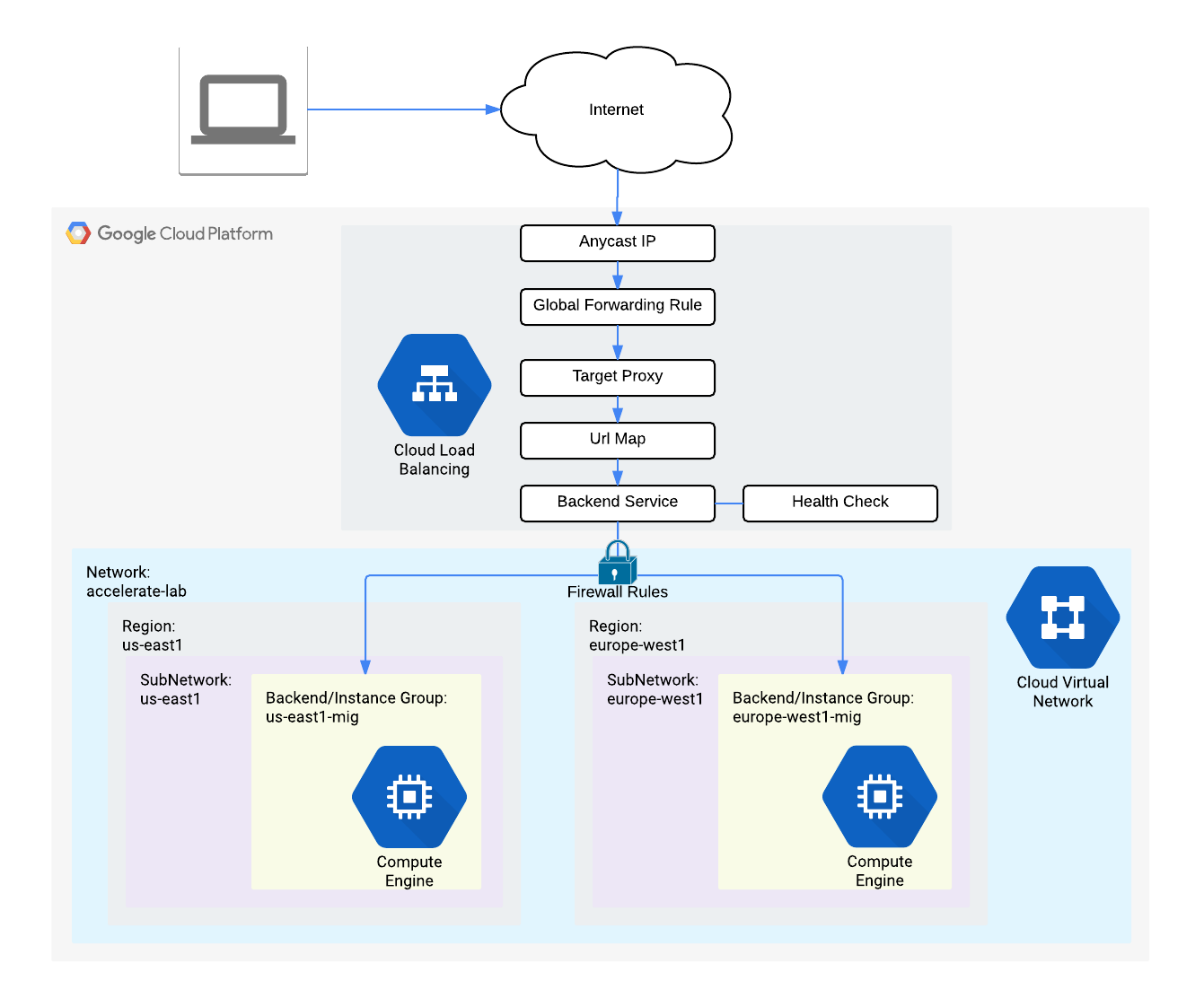
HTTP Load Balancer with Cloud Armor
- Theory
- Google Cloud HTTP(S) load balancing is implemented at the edge of Google's network in Google's points of presence (POP) around the world
- User traffic directed to an HTTP(S) load balancer enters the POP closest to the user and is then load balanced over Google's global network to the closest backend that has sufficient capacity available
- Cloud Armor IP allowlist/denylist enable you to restrict or allow access to your HTTP(S) load balancer at the edge of the Google Cloud, as close as possible to the user and to malicious traffic
- Create the HTTP firewall rule
- Health checks determine which instances of a load balancer can receive new connections
- Navigation menu > VPC network > Firewall > Create Firewall Rule
- Set values > Create
- Configure the instance templates
- Navigation menu > Compute Engine > Instance templates > Create instance template
- Click NETWORKING, DISKS, SECURITY, MANAGEMENT, SOLE-TENANCY > Management
- Under Metadata, click + ADD ITEM and specify the following
- startup-script-url - gs://cloud-training/gcpnet/httplb/startup.sh
- This script installs Apache and changes the welcome page to include the client IP and the name, region, and zone of the VM instance
- Networking > Done
- The network tag http-server ensures that the HTTP and Health Check firewall rules apply to these instances
- Create
- Create the managed instance groups
- Navigation menu > Compute Engine > Instance groups > Create instance group
- Verify the backends
- Configure the HTTP Load Balancer, Start the configuration
- Navigation menu > click Network Services > Load balancing > Create load balancer > HTTP(S) Load Balancing > Start configuration
- From Internet to my VMs or serverless services > Continue
- Configure the backend
- Backend configuration > Backend services & backend buckets > Create a backend service
- For Health Check, select Create a health check
- Health checks determine which instances receive new connections
- Configure the frontend
- Review and create the HTTP Load Balancer
- Test the HTTP Load Balancer - Stress test
- In SSH terminal
sudo apt-get -y install siege-=> Install siegeexport LB_IP=[LB_IP_v4]-=> To store the IPv4 address of the HTTP Load Balancer in an environment variablesiege -c 250 -t150s http://$LB_IP-=> To simulate a load- Navigation menu > Network Services > Load balancing > Click Backends > Click http-backend
- Navigate to http-lb > Click on the Monitoring tab > Monitor the Frontend Location (Total inbound traffic)
- Denylist the created instance - Create the security policy
- Navigation menu > Network Security > Cloud Armor > Create policy
- Verify the security policy
curl http://$LB_IP-=> To access the load balancersiege -c 250 -t150s http://$LB_IP-=> In the SSH terminal of siege-vm, to simulate a load
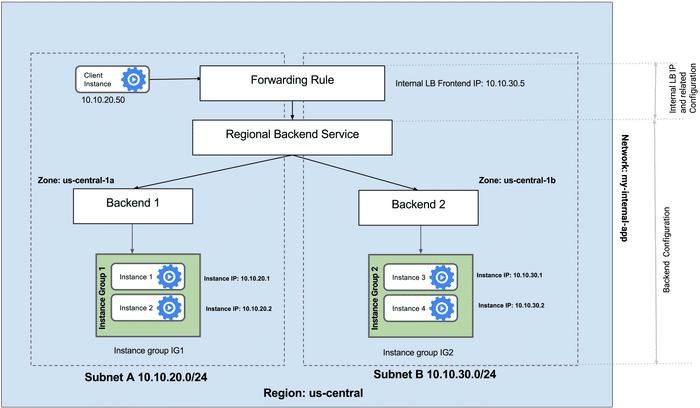
Create an Internal Load Balancer
- Theory
- Google Cloud offers Internal Load Balancing for your TCP/UDP-based traffic
- Internal Load Balancing enables you to run and scale your services behind a private load balancing IP address that is accessible only to your internal virtual machine instances
- Configure HTTP and health check firewall rules
- Configure instance templates and create instance groups
- A managed instance group uses an instance template to create a group of identical instances. Use these to create the backends of the Internal Load Balancer
- Configure the Internal Load Balancer
- Navigation menu > Network Services > Load balancing > Create load balance > TCP Load Balancing > Start configuration
- Internet facing or internal only > Only between my VMs > Continue
- This choice requires the backends to be in a single region and does not allow offloading TCP processing to the Load Balancer
- Configure the regional backend service
- Configure the frontend
- Test the Internal Load Balancer
Google Cloud Packet Mirroring with OpenSource IDS
- Theory
- Traffic Mirroring is a key feature in Google Cloud networking for security and network analysis. Its functionality is similar to that of a network tap or a span session in traditional networking
- Packet Mirroring captures network traffic (ingress and egress) from select "mirrored sources", copies the traffic, and forwards the copy to "collectors"
- Packet Mirroring is founded on a "Packet Mirroring Policy", which contains the following attributes
- Region
- VPC Network(s)
- Mirrored Source(s)
- Collector (destination)
- Mirrored traffic (filter)
- Key Points
- Only TCP, UDP and ICMP traffic may be mirrored. This, however, should satisfy the majority of use cases
- "Mirrored Sources" and "Collectors" must be in the SAME Region, but can be in different zones and even different VPCs, as long as those VPCs are properly Peered
- Additional bandwidth charges apply, especially between zones. To limit the traffic being mirrored, filters can be used
- One prime use case for "Packet Mirroring" is to use it in an Intrusion Detection System (IDS) solution
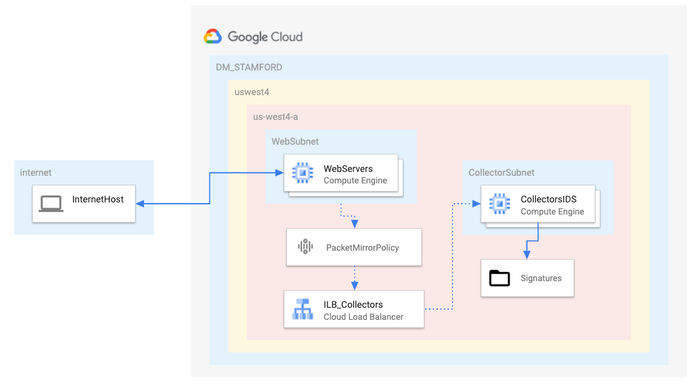
- Build a networking footprint
- Create a VPC and create 2 subnets inside that VPC
- Create firewall rules and Cloud NAT
- Rule 1 allows the standard http port (TCP 80) and the ICMP protocol to all VMs from all sources
- Rule 2 allows the IDS to receive ALL traffic from ALL sources. Be careful NOT to give the IDS VM a public IP in the later sections
- Rule 3 allows the "Google Cloud IAP Proxy" IP range TCP port 22 to ALL VMs, enabling you to ssh into the VMs via the Cloud Console
- Create a CloudRouter
- As a prerequisite for Cloud NAT, a Cloud Router must first be configured in the respective region
- Configure a Cloud NAT
- To provide Internet access to VMs without a public IP
- Create Virtual Machines
- Create an Instance Template for a WebServer
- Create a Managed Instance Group for the WebServers
- Create an Instance Template for the IDS VM
- Create a Managed Instance Group for the IDS VM
- Create Internal LoadBalancer
- Install Open Source IDS - Suricata
- SSH into the IDS VM
- Verify Installation
- Configure and review Suricata
- Download and replace new Suricata configuration file and abridged rules file
- Start the Suricata service
- Review Simple Suricata rules for testing
- Configure Packet Mirror Policy
- Test Packet Mirroring
- Generate traffic to the "mirrored" subnet
- Test Suricata IDS inspection and alerts
- TEST 1: Test egress UDP rule/alert
- TEST 2: Test egress "TCP" rule/alert
- TEST 3: Test ingress "ICMP" rule/alert
- TEST 4: Test ingress "HTTP" rule/alert